Introduction
This my work was inspired by reseaching of Marc Schink & Johannes Obermaier Exception(al) Failure - Breaking the STM32F1 Read-Out Protection.
Depend on proposed algorithm I've wrote utility that using vulnerabilty of Readout Protection mechanism of Stm32F1 cpu for partically disclosing contents of protected flash memory
Application
The exploit from authors of reseaching is writing on Python and need SEGGER J-Link debugger. Also it is need OpenOCD installed
Instead Stm32F1Discloser use St-Link debugger. It is windows application and don't need additional software. The only prerequisition is installed driver for St-Link debugger

Application has simple interface. It don't need installation and fully free for using.
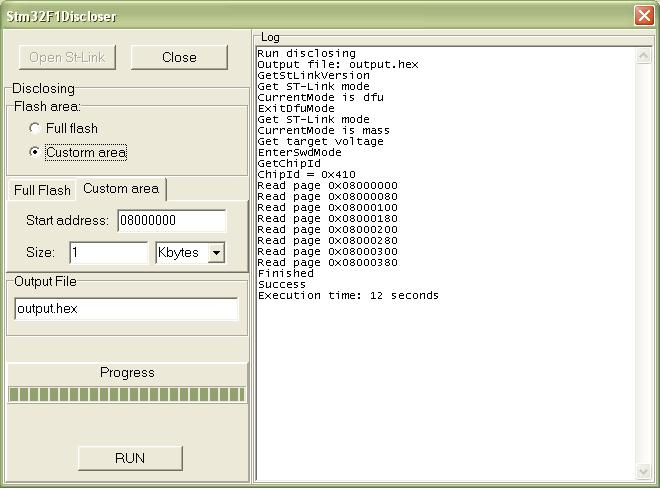
It is take about 25 minutes for discovering 128 kbytes flash memory.
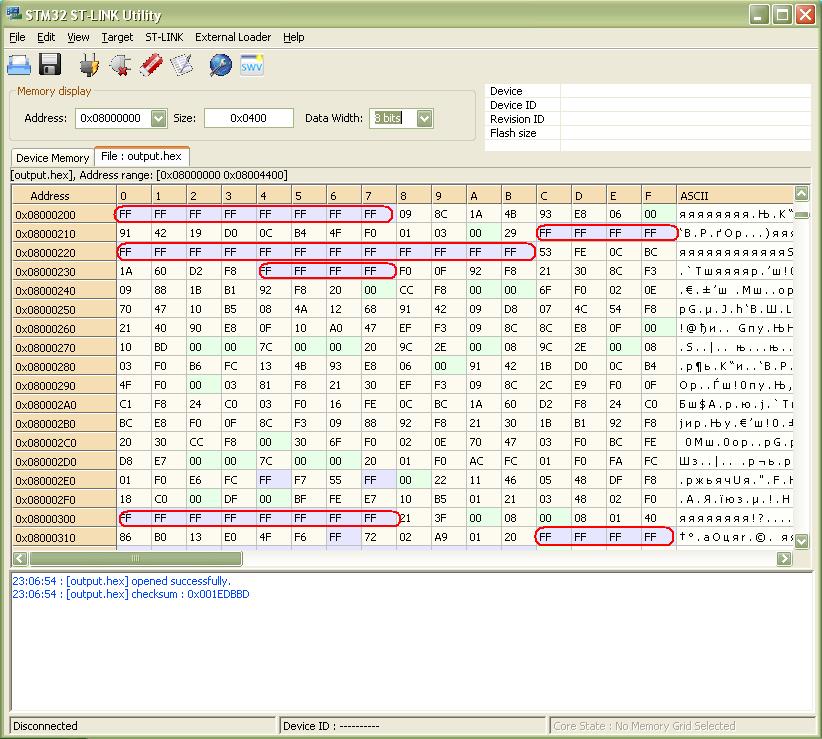
As it has been mentioned the discovering is not full. In every chunk of 256 byte it is 28 undiscovered bytes with addresses XXXXXX00-XXXXXX07, XXXXXX1C- XXXXXX2B and XXXXXX34-XXXXXX37. Application fill this areas with value 0xFF as is shown on next figure.
Downloading